Treasury sanctions hosting provider for crypto cybercrimes
U.S. Treasury’s Office of Foreign Assets Control sanctions Russia-based hosting provider Aeza Group LLC for enabling cybercriminal operations.
The action includes cryptocurrency address designation while targeting critical infrastructure supporting ransomware attacks and data theft activities globally.
OFAC sanctions Aeza Group network for bulletproof hosting services
On July 1, 2025, Aeza Group LLC, a Russia-based bulletproof hosting company, and its executives were sanctioned by the U.S. Department of Treasury’s Office of Foreign Assets Control for aiding cybercrime. The penalties cover both cyber-related and CAATSA Russia-related agencies, according to Chainalysis.
The whole global network, including Aeza International Ltd. in the UK and other affiliated businesses, is covered by OFAC’s action in addition to the main Russian firm. This comprehensive approach addresses the global scope of modern cybercrime infrastructure operations spanning multiple jurisdictions.
The designation continues OFAC’s focus on disrupting service providers who enable massive cyber threats by targeting essential infrastructure that fraudsters use to host illicit information. This action follows the February 2025 designation of ZServers.
Aeza Group provided bulletproof hosting services that allowed cybercriminals to conduct ransomware attacks, data theft, and other malicious cyber activities while maintaining operational security. The company’s services included dedicated servers advertised from Moscow-based locations, providing resilient hosting infrastructure for criminal operations.
The sanctions target the supply chain supporting cybercrime operations rather than pursuing individual threat actors after attacks occur. This addresses the foundational infrastructure that makes large-scale cybercriminal activities possible.
Treasury flags addresses linked to Aeza payment infrastructure
OFAC’s designation includes one TRON cryptocurrency address TU4tDFRvcKhAZ1jdihojmBWZqvJhQCnJ4F associated with Aeza Group’s payment infrastructure for illicit hosting services. On-chain analysis reveals that Aeza Group relied on payment processors to receive payments for hosting services, obscuring the traceability of customer deposits through intermediary systems.
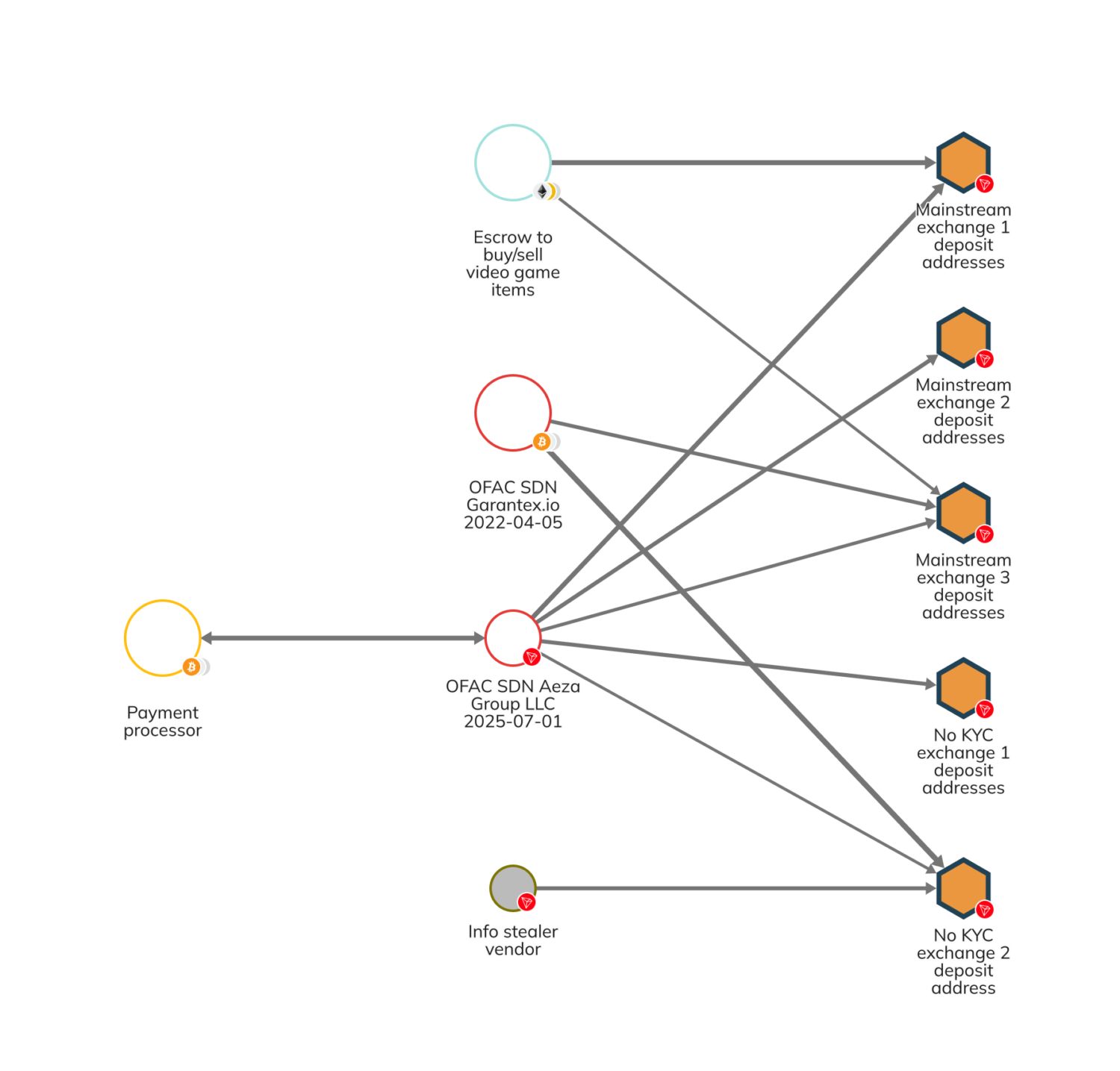
As an administrative wallet, the specified address manages cash-outs from payment processors, transfers money to other cryptocurrency exchanges, and occasionally gets paid directly for Aeza’s services. This wallet received more than $350,000 in cryptocurrency while cashing out at multiple deposit addresses across different exchanges.
The deposit addresses that Aeza utilized, according to Chainalysis Reactor study, also received money via an escrow provider for transactions on gaming platforms and the Garantex exchange. Additional connections include a darknet vendor selling infostealer malware, which breaches computer systems to steal sensitive user information.
This vendor was probably a client of Aeza since regular payments from the infostealer vendor wallet to Aeza’s exchange deposit address match Aeza’s hosting service pricing structures. The payment patterns provide evidence of the hosting provider’s direct involvement with malicious actors operating infostealers and other cybercriminal tools.
The detected TRON address has been marked by Chainalysis in their product suite, and they are still keeping an eye out for more addresses linked to Aeza and other reliable hosting services.
Targeting of cybercrime infrastructure disrupts criminal supply chains
Instead of going against specific threat actors after assaults have already taken place, OFAC’s action against Aeza Group targets the core infrastructure that enables large-scale cybercrime operations. This approach attacks the supply chain supporting cybercriminal activities by focusing on service providers that facilitate ongoing malicious operations.
Bulletproof hosting services like Aeza Group offer customized services resistant to takedown and law enforcement actions, providing high-level infrastructure for criminal use. The services facilitate constant access to hosting infrastructure needed for ransomware attacks, data thievery operations, and other malicious cyber activities.
Sanctions approach seeks to disrupt critical infrastructure dependencies used by cybercriminals for hosting malicious content and remaining online. Disrupting hosting services is meant by the authorities to make operationally difficult for cybercriminal groups that depend on robust infrastructure for running their operations.
This enforcement action follows similar disruptions of cybercrime infrastructure, including the February 2025 designation of ZServers, reflecting ongoing government dedication to disrupting service providers enabling criminality. This is a strategy of systemic disruption, rather than response to individual attacks.
KEY Difference Wire helps crypto brands break through and dominate headlines fast




