North Korean hackers target Web3 startups using fake Zoom meeting invitations
North Korean hackers have launched a sophisticated malware campaign targeting Web3 and cryptocurrency companies using NimDoor malware.
SentinelLabs identified advanced attack methods that combine social engineering with complex programming techniques to infiltrate Mac systems and steal sensitive information.
North Korean hackers trick victims through fake Zoom meeting updates
North Korean attackers begin their attacks by posing as known contacts through Telegram messaging, subsequently requesting their victims to organize meetings through Calendly scheduling pages. Victims are invited by email to download what appears to be a legitimate Zoom software update, with spoofed Zoom meeting links embedded.
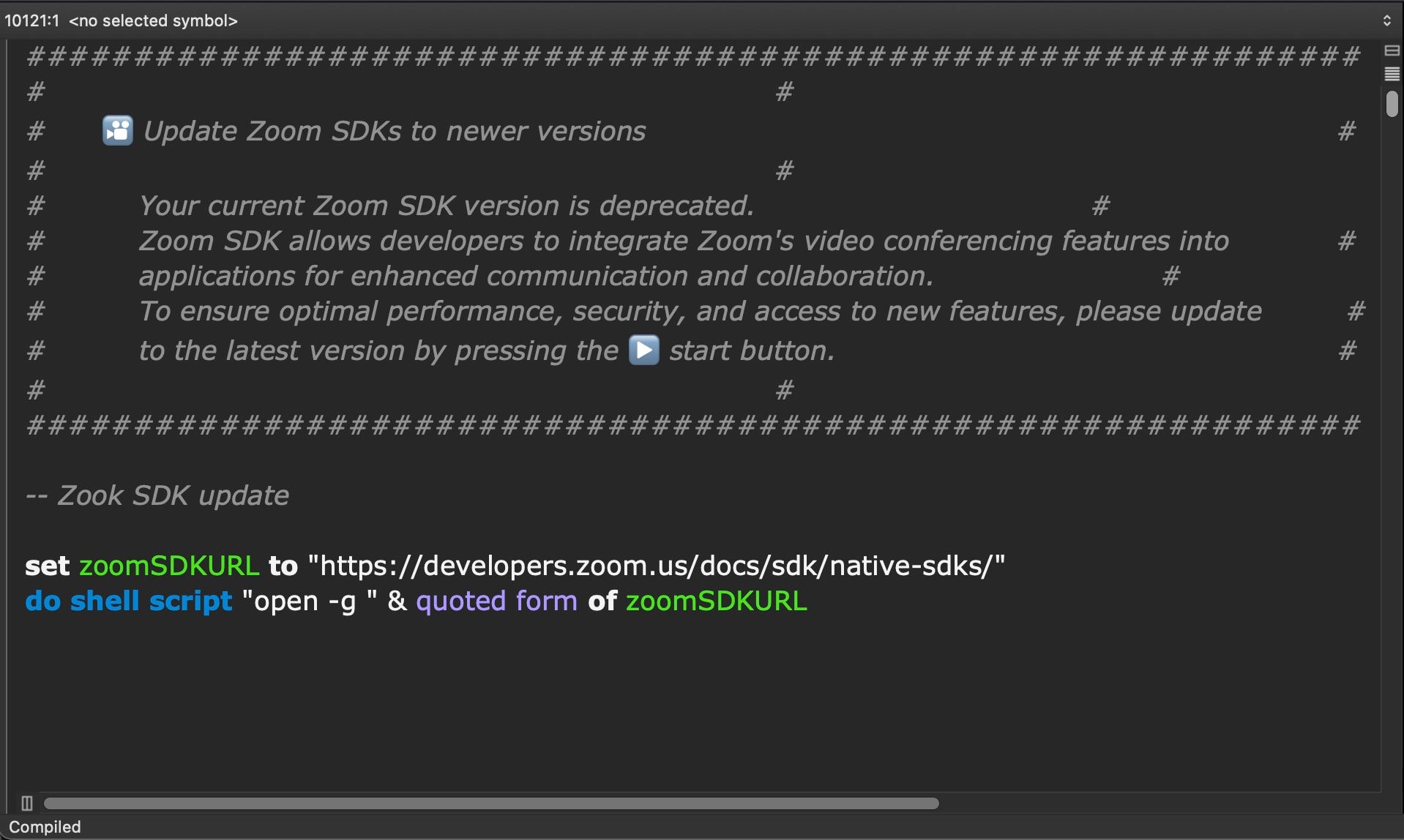
The attackers build domains that contain malicious files presented as Zoom support update files, with domain names that are designed to resemble actual Zoom meeting URLs. The spoofed domains contain variations such as support.us05web-zoom.forum and support.us05web-zoom.cloud, which are very similar to actual Zoom web domains known to users.
The attack programs have thousands of lines of empty space to hide their purpose, making them appear to be bigger and more natural than simple attack programs. Hidden in these programs are just three lines of attack code that download and run other attack modules from servers operated by the hackers.
SentinelLabs researchers discovered multiple concurrent domains used by the same attackers, which pointed to a wide-scale campaign that was impacting numerous victims with customized web addresses for each victim. The typos of the fake update files, like “Zook SDK Update” instead of “Zoom SDK Update,” are more easily detectable and trackable by security researchers.
Once the spoofed update is executed by victims, the malware loads a legitimate Zoom redirect URL with an HTML file. This presents the initial infection as legitimate while covertly initiating the primary attack components in the back. This is for the purpose of misleading victims into believing that they successfully executed a standard software update process.
NimDoor malware steals passwords and personal data
The NimDoor malware campaign uses two separate attack paths once it successfully infects victim computers. The first path focuses on stealing personal information including passwords, browser data, and chat histories from popular applications. The second path establishes long-term access to compromised systems through hidden background programs.
The malware targets multiple web browsers including Google Chrome, Firefox, Microsoft Edge, Brave, and Arc, copying stored passwords, browsing history, and saved login information. It also steals system passwords stored in Mac computers’ built-in password management systems and copies command history files that show what programs users have run.
A specialized component specifically targets Telegram messaging data, stealing encrypted chat databases and decryption keys that allow attackers to read private conversations offline. The stolen Telegram information includes both the encrypted message files and the special keys needed to unlock and read those messages.
All stolen information gets packaged and sent to attacker-controlled servers through encrypted connections. The malware creates hidden folders on infected computers to temporarily store copied data before transmission, using names designed to look like legitimate system files.
The attack uses advanced programming languages including Nim and C++ that many security programs have difficulty detecting. The malware includes features that help it avoid detection by security software, such as communicating through encrypted web connections and using legitimate-looking file names and locations.
The attackers designed the malware to work specifically on Mac computers, taking advantage of built-in Mac features to hide their activities and maintain persistent access to infected systems.
Advanced persistence methods ensure the malware survives
The NimDoor malware includes methods to maintain access to infected computers even after users restart their systems or attempt to remove the malicious software. The attackers use a clever approach that automatically reinstalls the malware whenever users try to terminate or delete it.
When users attempt to stop the malware process or shut down their computers, the malware catches these termination signals and immediately writes backup copies of itself to hidden locations on the infected system. This creates a situation where trying to remove the malware actually triggers its reinstallation process.
The malware creates fake system files with names designed to look legitimate, such as creating folders named after Google services but with subtle spelling differences that users typically do not notice. These fake files get automatic startup permissions that cause the malware to run every time the computer boots up.
A key component acts as a lightweight monitoring program that checks in with attacker servers every 30 seconds, sending information about running programs and waiting for new commands. This monitoring happens through seemingly innocent connections that appear similar to normal web traffic.
The malware also includes a 10-minute delay before becoming fully active, which helps it avoid detection by security software that scans for immediately suspicious behavior. This delay makes the malware appear like a normal program that takes time to start up.
These persistence methods by North Korean hackers make the malware particularly difficult for average users to remove completely. It also often requires specialized security tools or professional assistance to fully clean infected systems.
KEY Difference Wire: the secret tool crypto projects use to get guaranteed media coverage



