Kaspersky reports compromised mobile malware stealing users' crypto seed phrases
Kaspersky security researchers have uncovered a mobile malware campaign targeting cryptocurrency users through infected applications.
SparkKitty spyware reportedly steals device screenshots containing seed phrases using optical character recognition technology across iOS and Android platforms through official app stores.
SparkKitty malware infiltrates official app stores targeting crypto
Kaspersky researchers discovered the SparkKitty spyware campaign in January 2025, following their previous identification of SparkCat malware targeting cryptocurrency wallets. The new threat distributes malicious applications through unofficial sources as well as official Google Play and App Store platforms, with infected apps already removed from Google Play following researcher notifications.
SparkKitty attacks iOS and Android platforms with multiple delivery mechanisms for each. On iOS, malware payloads are delivered through frameworks that masquerade as legitimate libraries like AFNetworking.framework or Alamofire.framework, or obfuscated libraries masquerading as libswiftDarwin.dylib. The malware also inserts itself directly into applications.
Android operating systems employ both Java and Kotlin languages, with Kotlin versions employed as malicious Xposed modules. The majority of malware versions indiscriminately hijack all the images on devices, although researchers detected similar malicious clusters employing optical character recognition to attack specific pictures with sensitive information.
The campaign has been active since at least February 2024, and it has also shared targeting tactics and infrastructure with the previous SparkCat operation.
SparkKitty has a wider reach than SparkCat’s targeted attack on cryptocurrency seed phrases because it scrapes all images that are available from infected devices. This has the potential to harvest other kinds of sensitive financial and personal information stored in device galleries.
TikTok mods from obscure stores serve as primary infection vector
Kaspersky analysts initially came across the campaign when tracking regularly suspicious links that were propagating modifications of TikTok Android apps. The modified apps executed additional malware code when users launched main app activities.
The config file URLs were presented as buttons within the compromised apps, launching WebView sessions to display TikToki Mall, an internet shopping portal that takes cryptocurrency for consumer items.
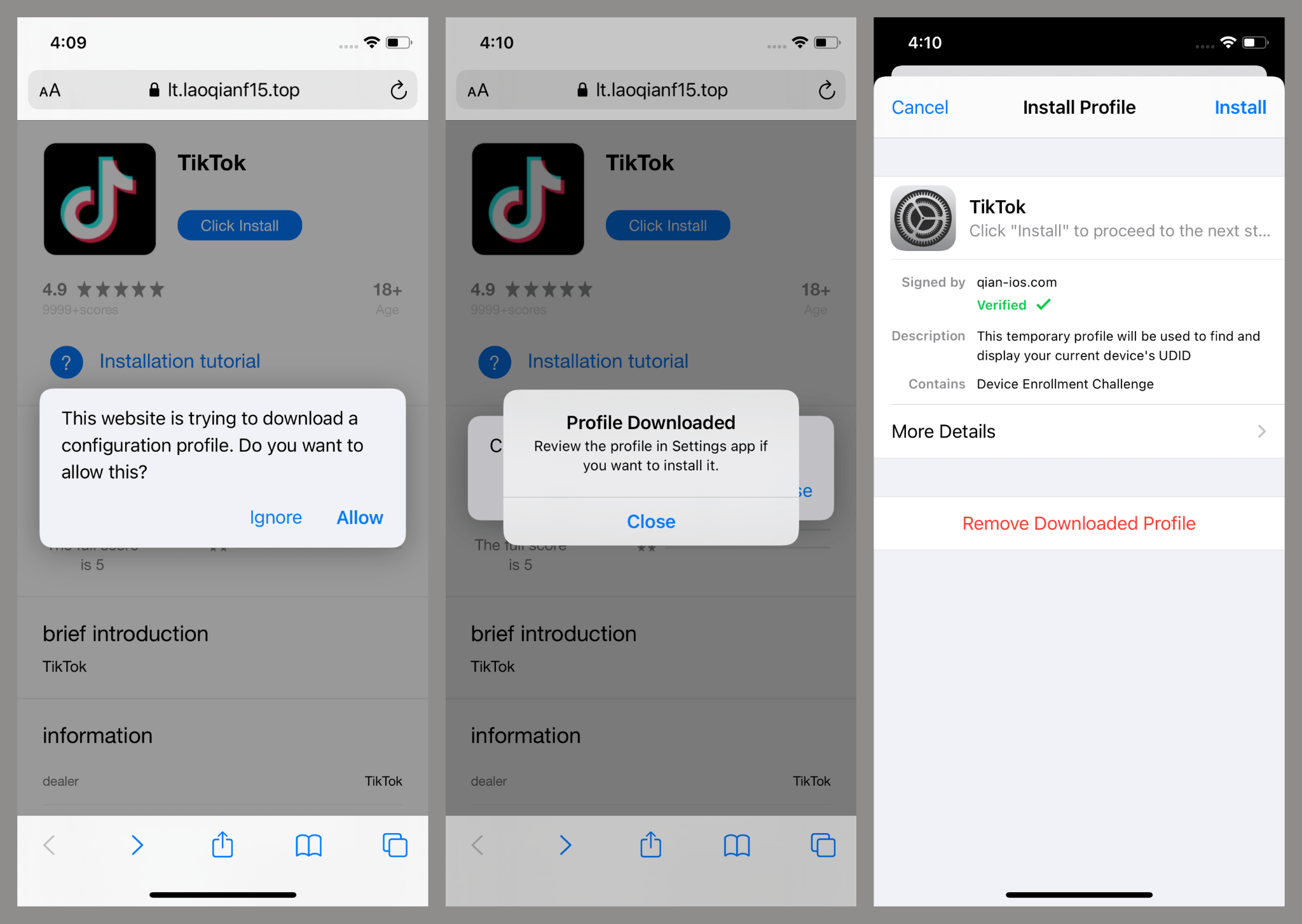
Registration and purchasing were restricted to require invitation codes, so researchers were unable to determine the store’s legitimacy or if it was operational. iOS infection vectors exploit Apple Developer Program enterprise profiles to circumvent normal app install restrictions.
Attackers hijack enterprise certificates for enterprise-level organizational app distribution, enabling malicious apps to install on any device without App Store approval. Enterprise profile misuse is one widespread tactic employed by developers of inappropriate apps such as online casinos, software cracks, and illegal modifications.
Infected versions of TikTok iOS applications request photo gallery permissions during startup, which is absent in genuine releases of TikTok. The malware is integrated into frameworks that pretend to be AFNetworking.framework and tampered AFImageDownloader classes and other AFImageDownloaderTool components.
Android malware variants steal images through cryptocurrency-themed applications
Android versions of SparkKitty operate through cryptocurrency-themed applications with malicious code embedded in entry points. The malware requests configuration files containing command and control server addresses, decrypting them using AES-256 encryption in ECB mode before establishing communication with remote servers.
Image theft occurs through two-stage processes involving device fingerprinting and selective upload mechanisms. The malware creates MD5 hashes combining device IMEI, MAC addresses, and random UUIDs, storing these identifiers in files on external storage.
Casino applications utilize LSPosed framework integration, functioning as malicious Xposed modules that hook application entry points. One infected messaging application with cryptocurrency exchange features reached over 10,000 installations on Google Play before removal following Kaspersky notifications.
Progressive web applications propagate through scam platforms advertising Ponzi schemes on popular social media platforms. These PWA-containing pages prompt users to download APK files that register content download handlers, processing JPEG and PNG images through Google ML Kit optical character recognition technology to identify text-containing screenshots.
Cryptopolitan Academy: Want to grow your money in 2025? Learn how to do it with DeFi in our upcoming webclass. Save Your Spot



